A well rounded security initiative has many security practices at a varying maturities. B-SIMM describes these practices, all in apart of a multi-year effort by the Cigital company to capture the essence of a good security lifecycle from different sectors in the industry (IV, Financial, Retail, etc…). The official list of companies are managed by Cigital. The metadata they provide is extremely useful to everyone participating in the area of lifecycle security.
In any organization that develops, purchases, or has a standing infrastructure for software design, build, and delivery will find these practices inherent in their program because they are the security practices you find in any practice. They show the maturity in “what you are currently doing” with those practices and “where you are heading” with them.
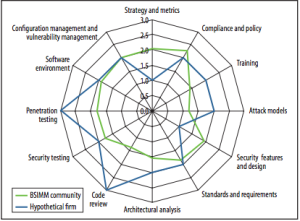
The B-SIMM is broken down into four domains: Governance, Intelligence, SSDL Touchpoints, and Deployment. All the security practices fall into one of those four domains as a sub-category of a domain. There are 12 sub-categories that hold 112 distinct practices at present. The security practice areas are shown below in a spider-chart.
An example of Security Practice Spider chart from an article by Gary McGraw at Cigital, http://www.cigital.com/presentations/mco2014030081.pdf
A spider-chart provides a quick dashboard level view of the maturity of those 12 security practice areas. Allowing for a quick contrast and compare across the current efforts in a software security initiative and how it compares to the general industry and industry sectors. A “high water mark” line allows for contrast measurements to be taken with lower-resolution security programs.
The 12 Security Practice areas are set across the four domains as below:
| Governance | Intelligence | SSDL Touchpoints | Deployment |
| Strategy and Metrics | Attack models | Architectural Analysis | Penetration Testing |
| Compliance and Policy | Security features and Design | Code Review | Software Environment |
| Training | Standards and Requirements | Security Testing | Configuration Management and Vulnerability Management |
Now, a secure Software Development Life-Cycle (SDLC) is needed to put those security practices into action.